Revil Ransomware Decrypt
On July 2 the REvil ransomware gang launched a massive attack against managed service providers around the world by exploiting a zero-day vulnerability in the Kaseya VSA remote management application. REvil gang asks for 70 million to decrypt systems locked in Kaseya attack.

Revil Revealed Tracking A Ransomware Negotiation And Payment
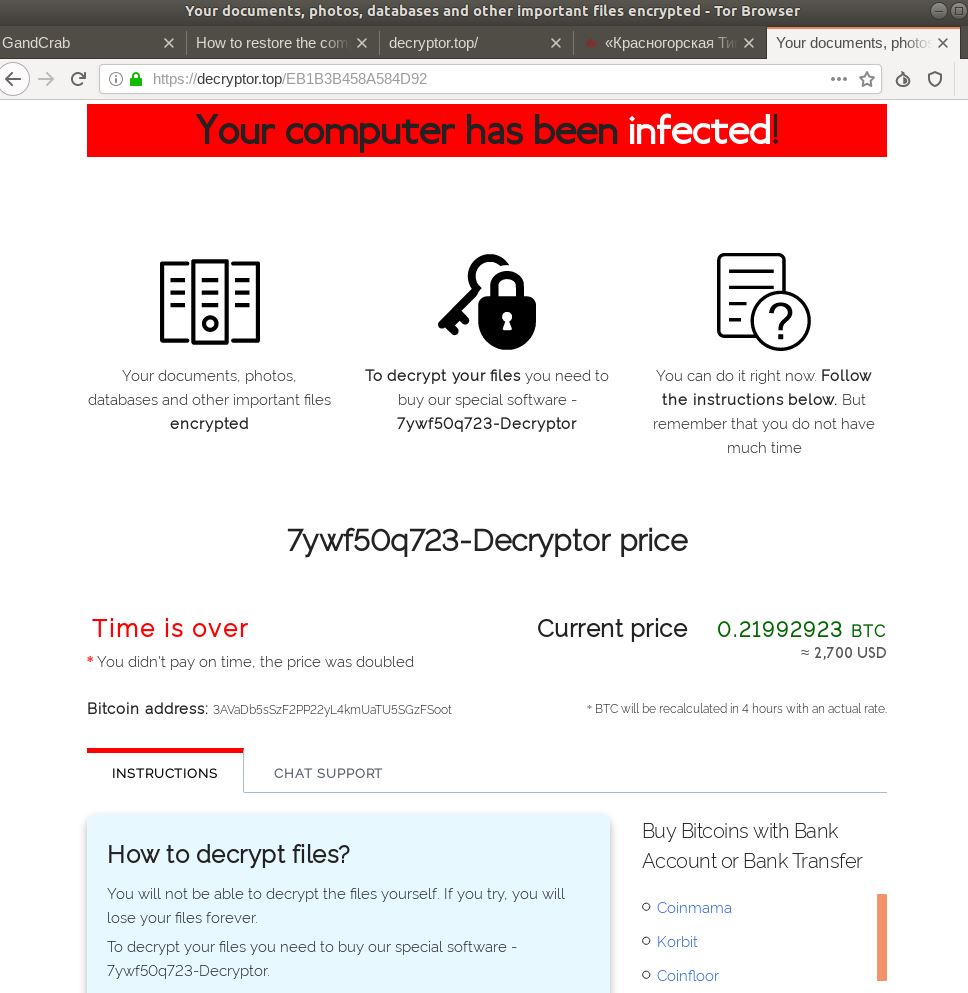
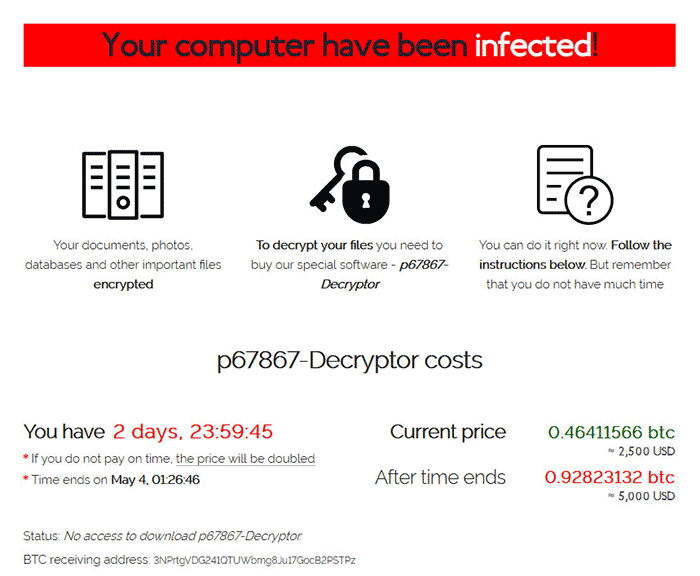
BlueBackground Ransomware or REvil Ransomware is disruptive cryptovirus that encrypts user data using Salsa20 algorithm with the ECDH-based key exchange method and then requires a ransom around 04750950 BTC to return the files.

Revil ransomware decrypt. In a message posted on their dark web blog the REvil gang officially took credit for the. Ransomware Universal Decryption Tool from REvils Cyberattack on Kaseya Leaks on Hacking Forum Tech Times. REvil is a ransomware-as-a-service RaaS operator that has extorted large sums of money from organizations around the world over the past year.
RaaS as variable as the criminals who use it. Kaseya the company that got hit by a large-scale REvil ransomware attack says it has obtained the official decryption key three weeks after the attack took place. No two criminal groups deploy the ransomware-as-a-service also known as Sodinokibi in exactly the same way.
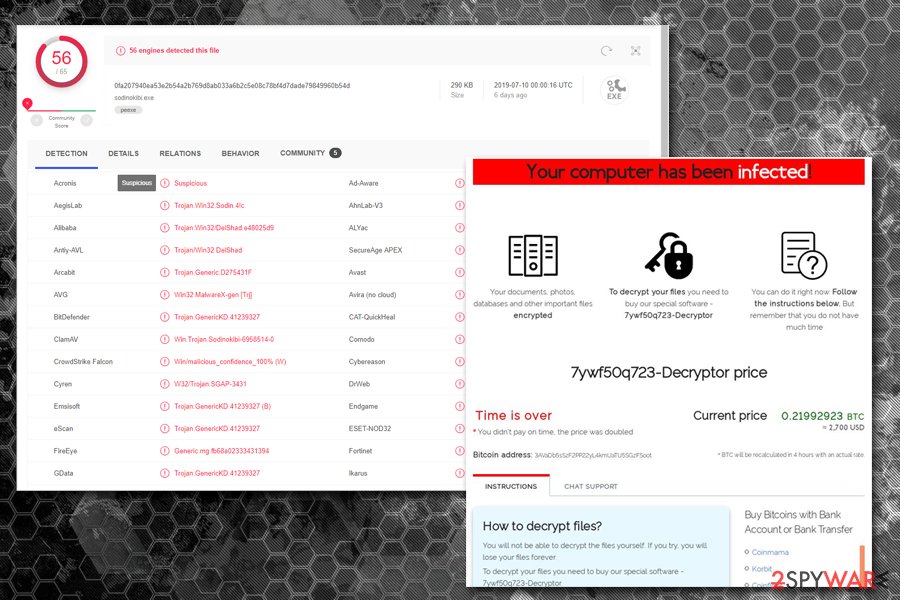
The universal decryption key for REvils attack on Kaseyas clients has been leaked on hacking forums allowing investigators to get a glimpse of the mystery key for the first time. When REvil ransomware victims pay a ransom they receive either a decryptor that works for a single encrypted file extension or a universal decryptor that works for all encrypted. Sodinokibi Ransomware aka.
A participant looks at. They started by patching a REvil universal decryptor with the decryption key leaked in the screenshot and after applying a patch to the decryptor they encrypted a virtual machine with some of the REvil ransomware samples used in the Kaseya attack. - contraction of Ransomware Evil - was inspired by the video game series - adapted in threadms - Resident Evil.
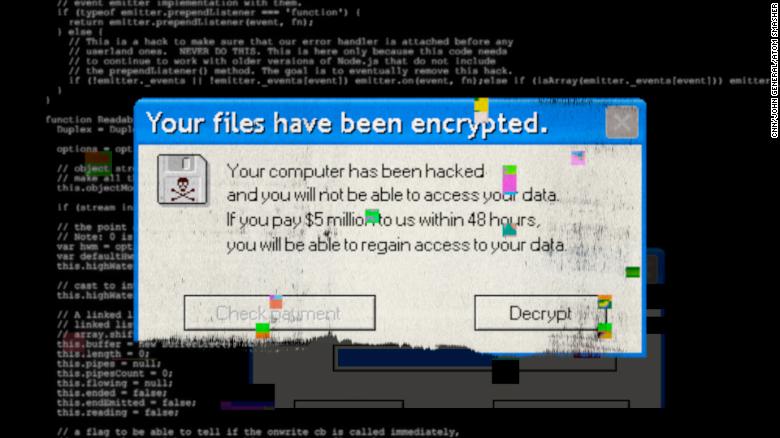
The transition to a service model of doing business transformed ransomware giving its developers the ability to focus on features and leaving the harder part. In other words if the amount is set at 2500 then without paying within 7 days it. Relentless REvil revealed.
Experts said it was absolutely possible for REvil to have created separate decryption keys for each victim but the ransomware group eventually came forward to offer Kaseya a universal decryptor. Through this chain reaction REvil was able to infect the systems and decrypt files of these many customers thus holding the data of all of them for ransom. REvil sold its ransomware as a.
REvil does this by parsing the 0x20 bytes RC4 key placed in one of its sections and verifying the checksum hash of the encrypted config file in its code body. Such a hack is known as a supply chain attack. REvil uses RC4 encryptiondecryption algorithm to decrypt its notable strings and its configuration file.
11 Aug The ransomware universal decryption tool that the clients of Kaseya used to obtain files held hostage by the REvil gang was leaked in a hacking forum. By Adam BerryGetty Images BERLIN GERMANY DECEMBER 27. The REvil ransomware gang is asking for a 70 million ransom payment to publish a universal decryptor that can unlock all computers locked during the Kaseya incident that took place this past Friday The Record has learned.
Kaseya Obtains Universal Decryptor On 7212021 Kaseya obtained a decryptor for victims of the REvil ransomware attack and were working to remediate customers impacted by the incident the official statement said. According to recent reports from security companies this is the most widespread ransomware threat and the group behind at the helm. This configuration file JSON format contains information and conditions on how it will encrypt the files in the compromised.
The REvil group combined the supply chain attack with a ransomware attack during which a companys IT. Last week an unnamed customer claimed to have paid a ransom to the REvil gang but was unable to decrypt encrypted files with the decryption key provided.
Remove Revil Ransomware Removal Instructions Recovery Instructions Included
Revil Ransomware Gang Inexplicably Vanishes From The Internet Cnn

Cto Perspective Examination Of The Revil Ransomware Attack

Revil Sodinokibi Ransomware Databreach Analysis Swascan
Remove And Decrypt Sodinokibi Ransomware Privacy Pc

Decryptor Released For Prometheus Ransomware Victims The Record By Recorded Future

Mcafee Atr Analyzes Sodinokibi Aka Revil Ransomware As A Service What The Code Tells Us Mcafee Blogs

Voicemail Icon Messages The Voice Voicemail
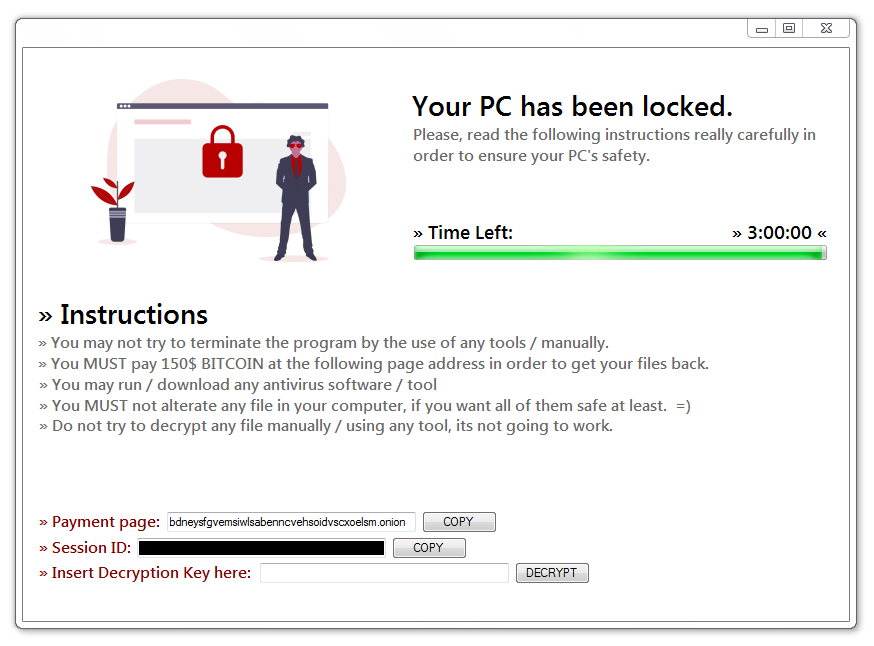
The Week In Ransomware May 15th 2020 Revil Targets Trump
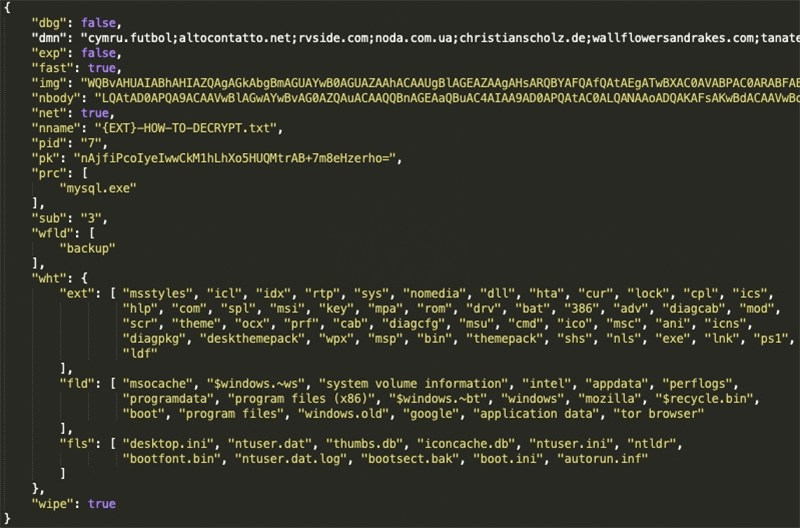
Revil Ransomware Removal Report

Computer Security Info Protects System From External Threat Computer Security System Restore Antivirus Program
Revil Ransomware Threat Research Update And Detections Splunk

Sodinokibi Ransomware Recovery Beforecrypt

Revil Ransomware Virus File Removal Decryption Methods
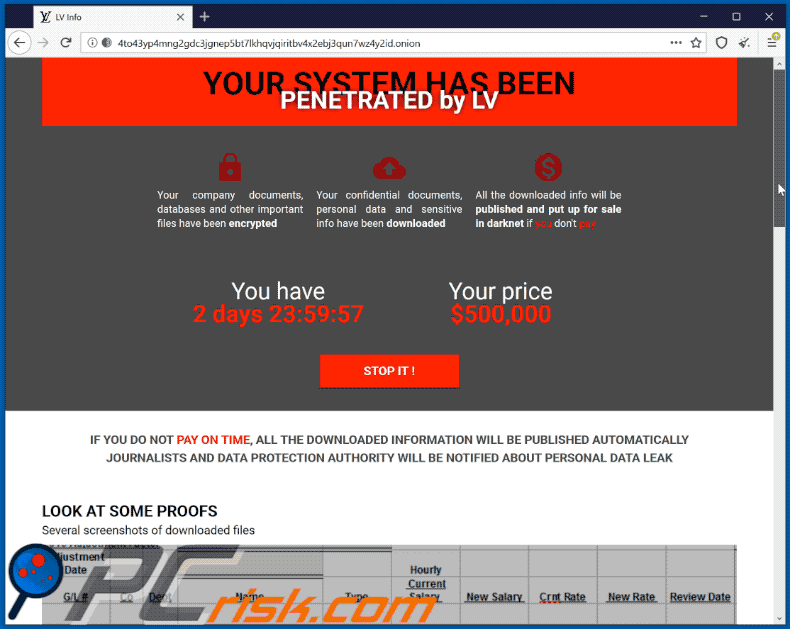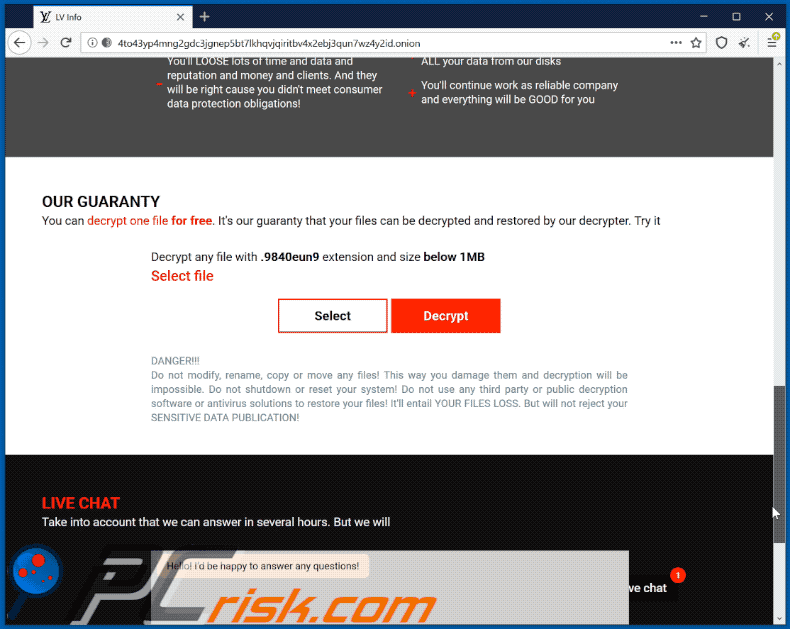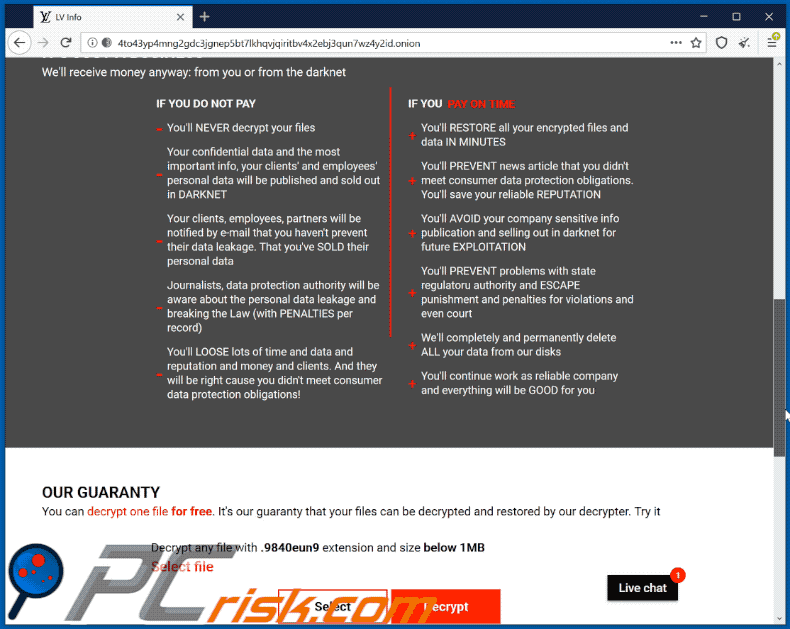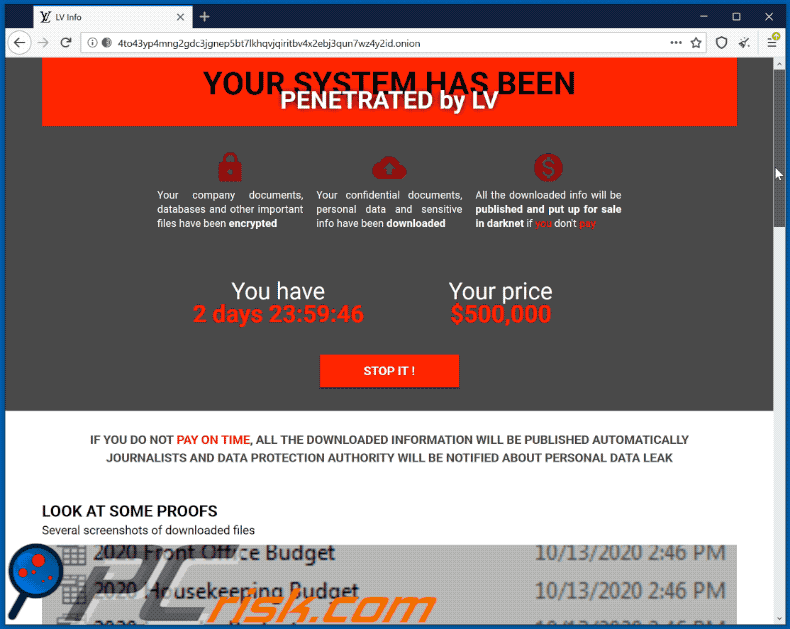
How To Remove Sodinokibi Ransomware Virus Removal Steps Updated

Sodinokibi Ransomware Analysis And Protection
Revil Ransomware Threat Research Update And Detections Splunk